The Samsung “Galaxy Apps” application installed on every recent Samsung device, a parallel store application with both apps for Samsung smartphones and smart watches, is vulnerable to MITM attacks which could cause user information leaks, permissions dialog bypass and session hijacking.
Affected Products
Samsung Galaxy Apps <= 4.1.01-14

MITM, Information Leaks and Session Hijacking
Summary
Most of the application API requests are made through a unsafe HTTP connection which would allow a malicious third party to perform a network MITM attack and eventually exfiltrate user sensitive data such as his session identifier and subsequently use this data to impersonate the user session.
Details
The application relies on a XML based API used through HTTP, as soon as the user will open the app and start browsing a network attacker will be able to see requests sent to the API server and the user session data, for instance the first request being executed when the user clicks on an application detail page, identified by the name productDetailOverview is composed as shown in the following picture.
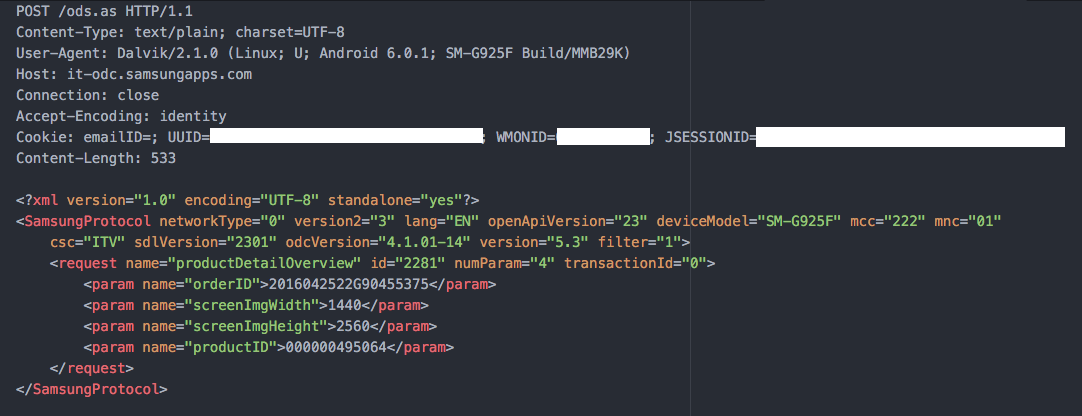
The XML response will contain application data such as the creation date, last update date, product name and description, etc.
It is possible to see that the user session cookies ( UUID and JSESSIONID ) are sent in cleartext, therefore they can be used by an attacker to impersonate the user and perform API requests on his behalf.
Other XML request names sent during application browsing and installation are:
- bigBannerList, used to obtain application preview images.
- expertCommentList and commentList, these fetch comments for an app.
- productDetailRelated, fetches related applications list.
- categoryProductList2Notc, fetches products in the same category.
- sellerProductList2Notc, fetches other products of the same vendor.
- androidManifestList, fetches the list of permissions required by the application before installing it ( more on this later ).
Impact
- User Impersonation - An attacker could use the exfiltrated session data to authenticate against the API server on the user’s behalf.
- Contents Manipulation - With a transparent proxy and proper redirection rules, an attacker could intercept and modify the XML responses before they’re received by the application, this would allow him to replace product images, names and descriptions with fake ones.
Permissions Dialog Bypass
Summary
It is possible for an attacker performing a MITM network attack to intercept and modify the XML response of the androidManifestList request and force the product to install an application without showing to the user the permission list dialog which would require his approval.
Details
Once the user clicks on the “Install” button, an androidManifestList request is sent to the API endpoint in order to fetch the list of permissions that the application requires:
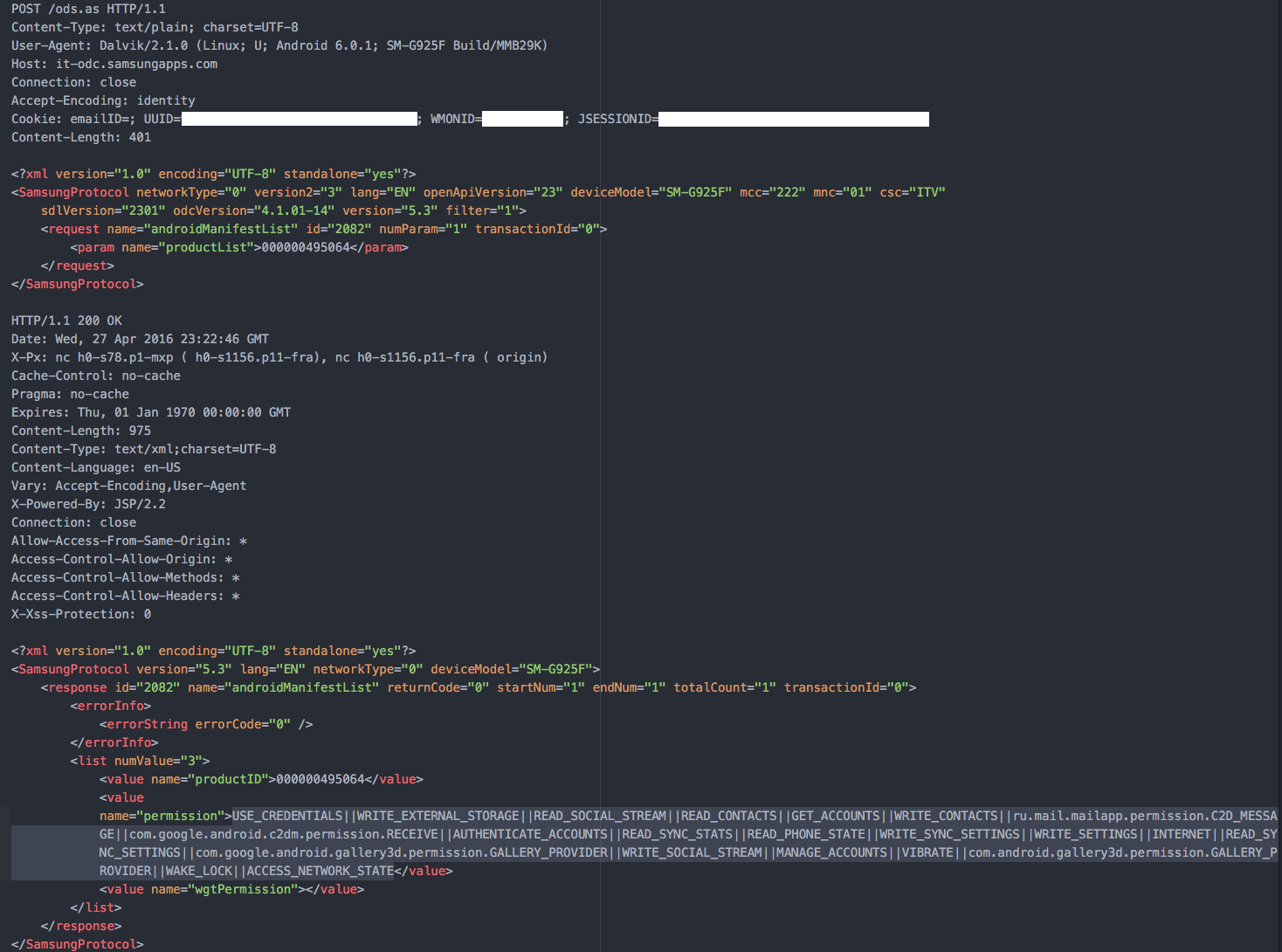
As shown in this picture, the response will contain the list of permissions separated by a double pipe ( “||” ) token.
This list is then splitted by the application and the user is prompted with a dialog which shows him the required permissions, the installation process requires the user to accept all of them in order to successfully continue.
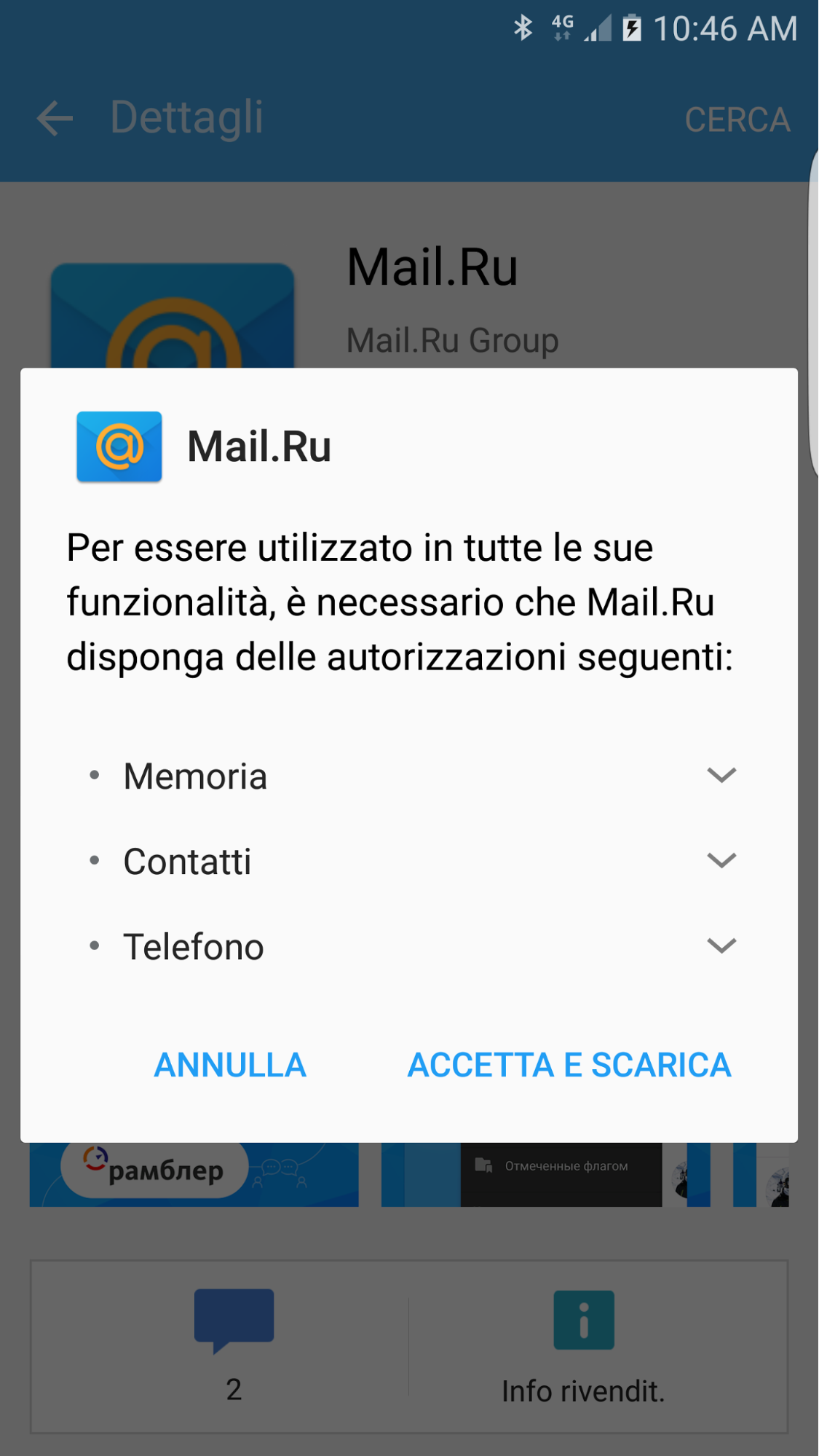
An attacker performing a MITM network attack can intercept and modify the XML response for this API before it’s sent to the device and replace the permissions list with a single INTERNET permission entry, in this case the Samsung Galaxy Apps store will directly install the application without showing the user any dialog at all.
The following is a POC bettercap proxy module.
1 | =begin |
Impact
An attacker could trick the user to think that an application which requires sensitive permissions does not require any at all, thus forcing the store to install it without any kind of user manual approval.
Mitigations & Recommendations
- Use HTTPS connections for every API request.
- Implement SSL key pinning to avoid SSL MITM attacks.
- Double check the list of permissions after the application is downloaded reading them directly from its AndroidManifest.xml file.
Disclosure Timeline
- May 2 2016 : Initial disclosure.
- June 7 2016 : Follow up.
- June 8 2016 : Email from vendor working on fixes.
- June 9 2016 : Confirmation that fixes were going to be pushed in next release
