SuperFish AdWare Found Inside X-Notifier Browser Extension Code.
You probably already heard about SuperFish around the web, an adware that Lenovo pre-installed on its computers since mid-2014. The danger does not reside inside the adware itself, that basically just injects some advertisment inside user web searches, but in the fact that, in order to handle HTTPS search engines ( Google ), it installs a root CA on the computer and replaces every HTTPS certificate sent by the web server with this one, leaving the victim vulnerable to SLL man in the middle attacks.
As soon as I heard the name “SuperFish”, it suddenly was somehow familiar to me … “Where the hell did I hear this name before?”
And there it goes, I have the X-Notifier browser extension installed on Google Chrome, wich is very useful to handle multiple gmail accounts at once without using a desktop email client, this is its options panel:
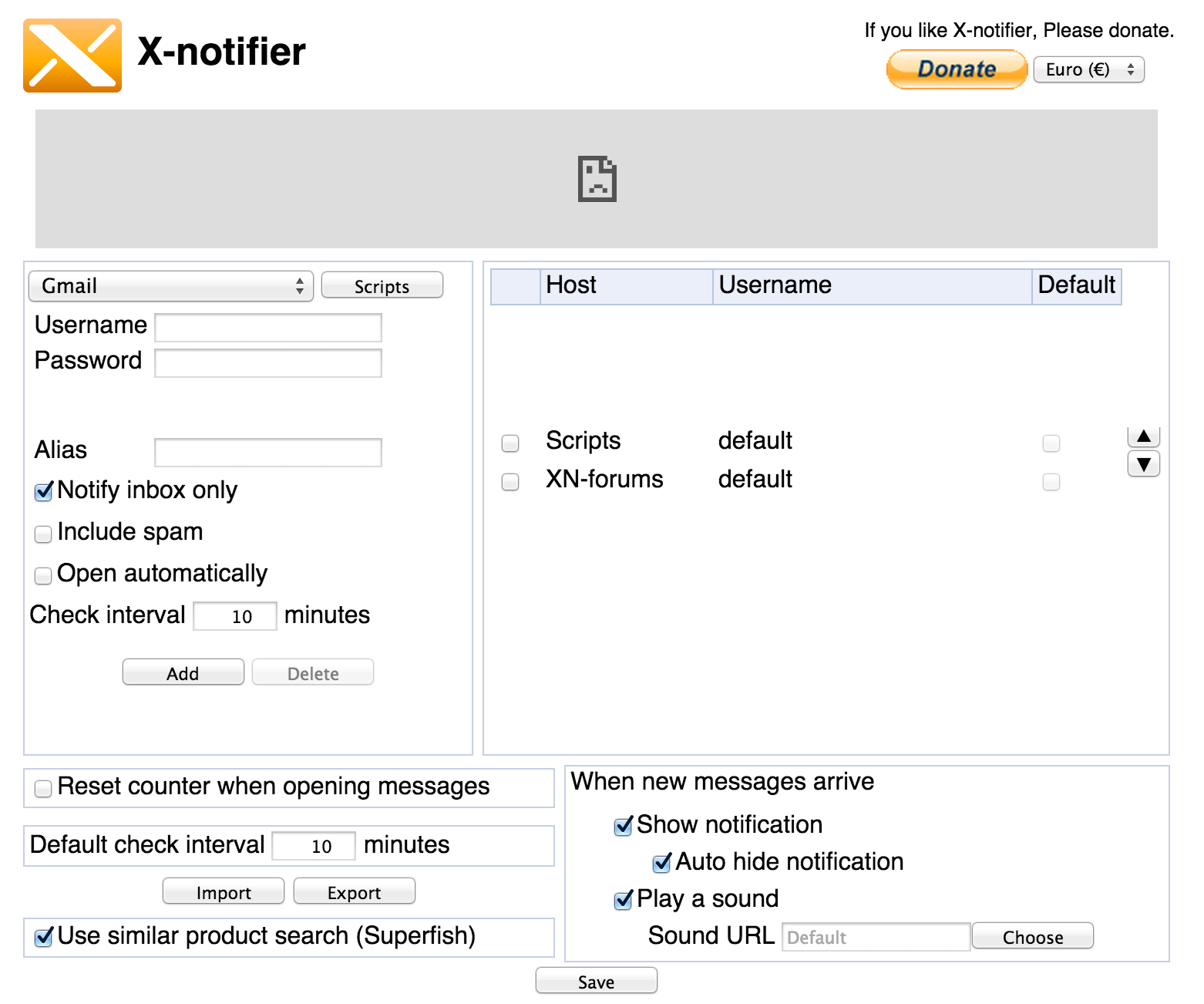
Look at the bottom left of the picture …. there you go, the extension offers an optional ( but turned on by default ) SuperFish injection :D
When enabled, you will find this request for each page you visit:
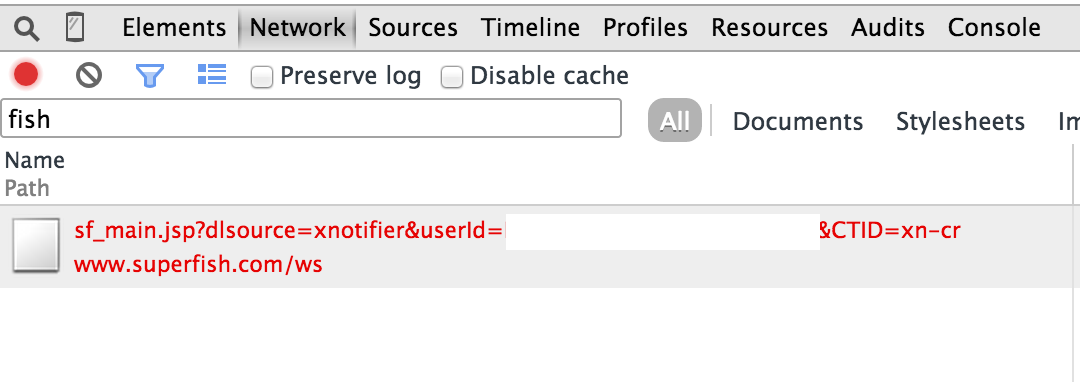
And here’s the code ( xnotifier/js/inject.js ):
1 | document.addEventListener('DOMContentLoaded', function () { |
Fortunately the server seems to be down, but the domain itself is still active:
Registrant Org: Superfish Inc. is associated with ~1 other domains
...
Domain Name: SUPERFISH.COM
Registrar: GODADDY.COM, LLC
Sponsoring Registrar IANA ID: 146
...
Updated Date: 21-sep-2014
Creation Date: 16-oct-2005
Expiration Date: 16-oct-2017
...So, apparently, Lenovo is not the only to use SuperFish services, that btw is not only an adware, but a whole company selling ads.